How I Became a Security Researcher
To be clear, I don't consider myself a security researcher, rather I am a programmer who happens to dabble in security research. Maybe this is a little bit of imposter syndrome kicking in, but I really think I just know enough to be dangerous.
A few months back I learned of the Online Services Bug Bounty program Microsoft was offering. I decided to give it a go. I am always looking for authorized hacking opportunities and really wasn't expecting anything to come of it. I created my test tenants and started playing around. I decided to focus on XSS vulnerabilities, as that is something I am pretty comfortable with and is pretty easy to test client side. Whenever I have tested for XSS vulnerabilities, I have always found that dialog windows tend to be some of the biggest culprits, so I honed in on those in my test tenant.
Eventually I stumbled across an OWA dialog that wasn't escaping strings. I was easily able to generate this (URLs hidden to protect the innocent):
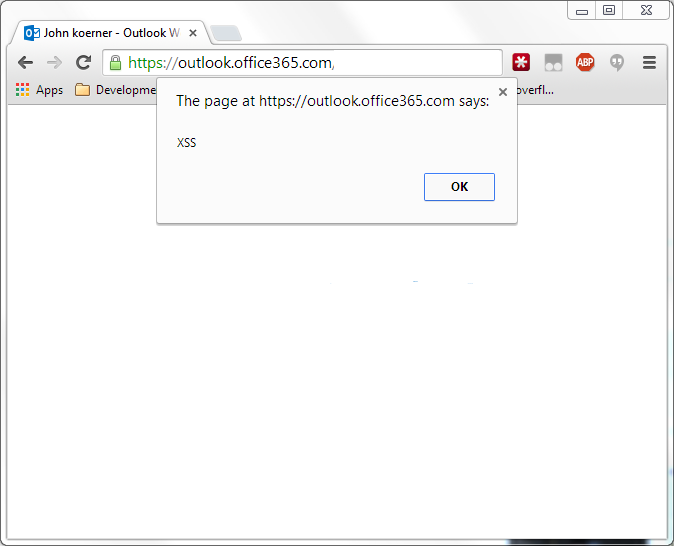
And then with a little more tweaking, this:
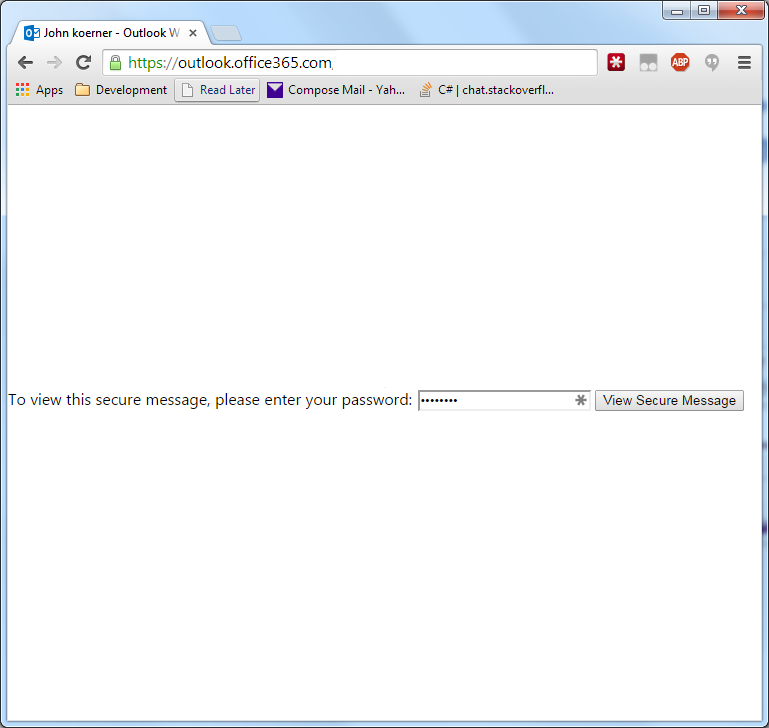
It was clear I had found an XSS vulnerability. I followed the submission instructions on the bug bounty page and waited to hear back. Within a few days, I got an email from the Microsoft security team indicating they had forwarded the bug to the product team. About a week after that I received confirmation that the product team had reproduced the bug and were working on a fix. Here is the timeline for the fix:
Oct. 9 (Thursday) - Reported Bug
Oct. 13 (Monday) - Microsoft confirmed receipt of bug
Oct. 21 (Tuesday) - Product team confirms repro of bug
Oct. 29 (Wednesday) - Product team confirmed that bug exists in boxed products
Dec. 9 (Tuesday) - Official security bulletin released.
Since this bug impacted user installed versions of exchange, it took a bit longer for the product team to fix. I didn't continuously test the online URL to know exactly when it was fixed, but I know as of today the vulnerability is fixed.
The bulletin for the bug is MS14-075.
The Microsoft team has credited me for this fix in multiple locations: